Uses Malware's Defenses Against It
Shaping Attackers Decision Making
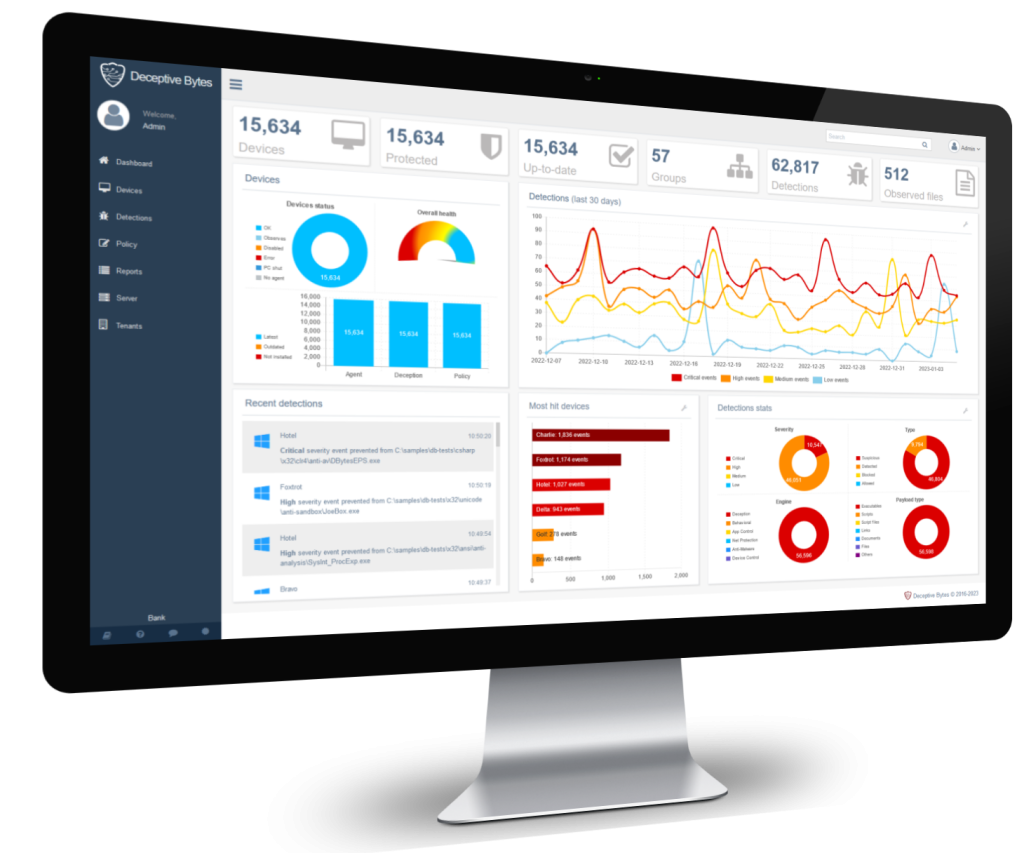
Deceptive Bytes offers an innovative cybersecurity solution designed to protect enterprises’ most critical and exposed assets: their endpoints. Our cutting-edge technology ensures robust defense against advanced threats, safeguarding your business from potential attacks. By focusing on endpoint protection, Deceptive Bytes helps maintain the security and integrity of your enterprise’s essential systems and data. Choose Deceptive Bytes for reliable and comprehensive endpoint security.
Our fully endpoint-centric prevention and deception platform offers advanced protection by creating dynamic and deceiving information to combat the evolving threat landscape. This solution interferes with attackers’ attempts to recon the environment, deterring them from executing malicious intents at every stage of the Attack Kill Chain. It effectively covers advanced and sophisticated malware techniques, ensuring that all endpoints and data in your enterprise remain secure. With our platform, you can stay ahead of threats and safeguard your business against even the most sophisticated cyber attacks.
Preemptive & Proactive
=> Prevents unknown & sophisticated threats
=> Very high prevention & detection rates
=> Real-time detection & response
Lightweight
=> Extremely low resource consumption (CPU, RAM)
=> System-wide protection with pinpoint handling
=> Deploys in seconds
Signature-less
=> NO constant updates
=> Can operate outside the corporate network
=> Stop millions of threats using 1 defence evasion technique
Reliable
=> High stability – operates in User-mode
=> Automatically approves legitimate processes
=> Low to a non-existing false positive rate
About Deceptive Bytes
Deceptive Bytes is a leading cybersecurity company specializing in endpoint security and threat deception. Our solutions empower organizations to protect their networks, devices, and data from cyber threats with proactive prevention, detection, and mitigation strategies. Using advanced deception techniques and real-time threat intelligence, we offer robust defense mechanisms against cyber attacks.
Our flagship product is an innovative endpoint protection platform that employs deception technology to trick cyber attackers into revealing their presence. By deploying decoys and traps that mimic legitimate assets such as files, applications, and systems, our platform detects, analyzes, and responds to threats in real-time, while also gathering valuable threat intelligence.
Designed for ease of deployment and minimal impact on system performance, our platform integrates seamlessly with existing security solutions, including SIEM (Security Information and Event Management) systems, and supports a wide range of devices, including Windows, macOS, and Linux systems.
In addition to our endpoint protection platform, Deceptive Bytes offers comprehensive services such as threat intelligence, incident response, and training to help organizations enhance their security posture. Choose Deceptive Bytes for cutting-edge cybersecurity solutions that keep your enterprise secure.
GET CURRENT LOCATION & ASSETS
Finds indicators to target’s location & assets, navigates inside the organization.
CHECK ENVIRONMENT INFORMATION
Querying the system for relevant information prior to attacking the endpoint or corporate network.
It contains payloads to evade current security tools and stops malicious behaviour upon possible detection.




