G Data Antivirus

German Quality Security?
G Data CyberDefense

G DATA ANTIVIRUS
Innovative
Best G DATA protection for Windows: Our brand new DeepRay® and BEAST technologies use artificial intelligence and behavioral analysis to detect camouflaged and previously unknown malware.
Smart
Our Next-Generation-Technologies already recognize by the behavior of programs whether they are planning an attack. So you are always one step ahead of hackers.
Uncompromising
Whether it’s attacks by ransom blackmailers, security breaches or online banking, you’re safe. A good feeling, isn’t it?

G DATA INTERNET SECURITY
Innovative
Best G DATA protection for Windows: Our brand new DeepRay® and BEAST technologies use artificial intelligence and behavioral analysis to detect camouflaged and previously unknown malware.
Secure on the Internet
Attacks during online banking and shopping, dubious websites, suspicious e-mails? No problem. Just keep on using the Internet and we’ll take care of the rest.
Made in Germany
Your data is sacred to you? We can understand you well. That’s why we attach great importance to maximum data security. And ensure that your data remains yours. Guaranteed.

G DATA TOTAL SECURITY
Innovative
Best G DATA protection for Windows: Our brand new DeepRay® and BEAST technologies use artificial intelligence and behavioral analysis to detect camouflaged and previously unknown malware.
Simply cleverer
Photos, videos, documents: Back up your data automatically and save the copies on your PC or in the cloud. Now nothing can go wrong.
No need to remember passwords
Password123? Better not. Our password manager remembers all your passwords for you and creates new ones on demand that can’t be cracked.
G DATA Antivirus features
Virus scanner
Put your trust in the highest detection rates with technologies working in parallel.
Behavior monitoring
Protect yourself against even unknown malware. G DATA Antivirus detects unknown malware with its unique behavior monitor scanner
Email scanning
Scans incoming email and attachments for suspicious content. Dangers are detected before anything has happened.
Anti-Ransomware
No opportunity for extortion Trojans – we stop criminals encrypting your files.
Exploit protection
Protects your computer against criminals exploiting security holes in Office applications and PDF readers, for example.
G DATA BankGuard
Our patented technology secures your browser against manipulation by data thieves – for secure online banking and shopping.
USB Keyboard Guard
Protects you against manipulated USB devices that pretend to be keyboards, even though they look like USB sticks or external hard drives.
Update Management
Specify when and where your PC loads updates. This helps you avoid additional costs, by logging into a third-party WLAN for example.
G DATA Internet Security features
Firewall
Monitors all incoming and outgoing connections to protect against hackers and spyware – fully automatically or according to your own rules.
Cloud-Backup
Automatically store your encrypted backups in the Cloud – using Dropbox or Google Drive.
Anti-Ransomware
No opportunity for extortion Trojans: Internet Security stops criminals encrypting your files.
G DATA BankGuard
Our patented technology secures your browser against manipulation by data thieves – for secure online banking and shopping.
Anti-Spam
Stops spam such as advertising and phishing emails and keeps your mailbox clean.
Parental Controls
Control your children’s Internet usage. Specify times and only let your children surf to approved sites.
Virus scanner
Put your trust in the highest detection rates with technologies working in parallel. Receive new virus signatures every hour, for the best protection against malware.
Exploit protection
Protects your computer against criminals exploiting security holes in Office applications and PDF readers, for example.
G DATA Total Security features
Anti-Ransomware
No opportunity for extortion Trojans: our Anti-Ransomware technology detects extortion Trojans before they can take your data hostage. We protect you against criminals trying to encrypt your photos, documents and personal data.
Password manager
This function memorises your passwords for online shops, forums, your email account and much more. Simply integrate our Password Manager into your browser. Passwords and contact data are filled in automatically if required.
Backups
Automatically back up your data locally on your PC or in the Cloud. With password-protected backups, your data always stays protected. Use Google Drive or Dropbox for your data backup.
Performance-Tuner
Delete outdated cache entries and other ballast. Improve the performance of your PC with a few clicks.
G DATA BankGuard
Make your banking transactions and online shopping secure – with our patented BankGuard technology. This function ensures that your browser only displays genuine content.
Access control
Specify who is allowed to use USB sticks, burners, hard drives and other devices on your PC. With Access Control, you can manage the use of all your USB slots. This will stop malware getting onto your computer via external storage media.
Browser Cleaner
Tidy up properly – with our Browser Cleaner you can remove unwanted toolbars and add-ons from Internet Explorer, Firefox and Chrome.
Encryption
Protect confidential information and files with a password. Then they can only be accessed by people you genuinely trust. Also encrypt external storage media such as USB sticks in this way. Encrypt them by simply using your secure password – without having to install software first.
Why G DATA?
End-to-end cyber defense
G DATA developed the world’s first antivirus software in 1987. Today, we defend our customers against all kinds of cybercrime with end-to-end solutions and services using the most advanced security software and AI technologies and even offering online security awareness training to teach safe behavior to employees.
Always there for you
G DATA customer support is available 24/7/365, with support teams and the G DATA SecurityLab working hand-in-hand at the same location.
Independent tests prove
that G DATA IT security solutions provide best attack detection rates for effectively combating Trojans, malware and even unknown viruses.
G DATA for Business
Reliable detection of known malware
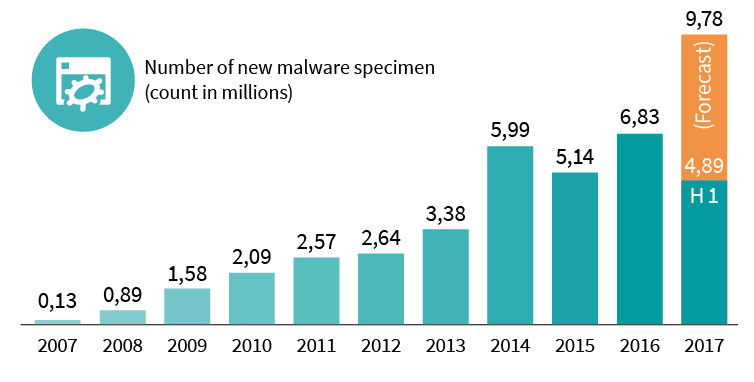
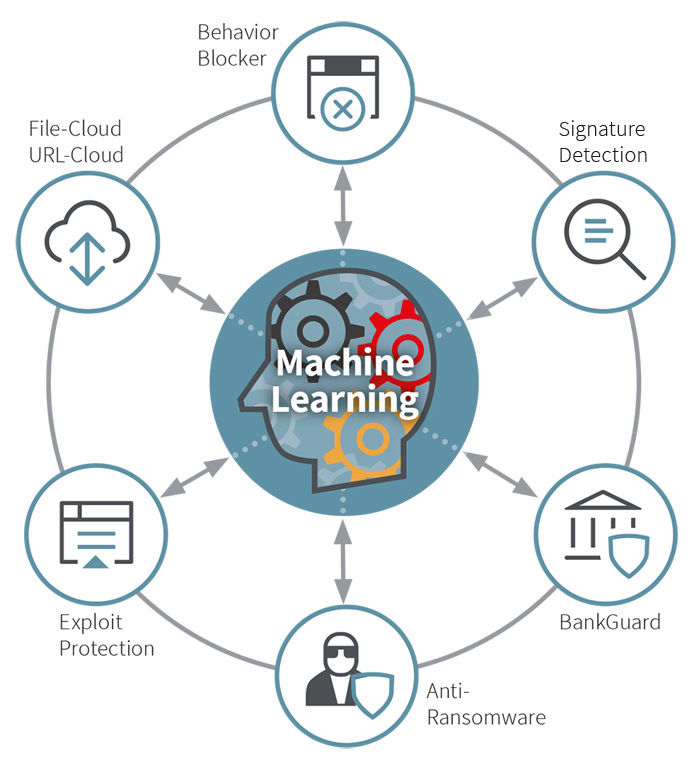
Next Generation Proactive Technologies
G Data Antivirus Business

- Virus monitor with CloseGap hybrid technology
- Anti-Ransomware Behaviour monitoring of files
- Protection against security vulnerabilities in installed software
- Online banking and browser protection
- Protection against malware and phishing when surfing
- Protection against manipulated USB devices
- DeepRay AI technology
- Light Agent for virtual machines
- Samba File Server Security
- Real-time protection
- Theft protection
- App and contact filter Report Manager
- Software/hardware directory
- Simple (remote) administration with guideline inheritance
- Clear dashboard
- Deployment on non-dedicated server also possible
- Active Directory connection
- Multi Tenancy
- Patch Management *optional purchase

G Data Client Security Business
- Virus monitor with CloseGap
- hybrid technology
- Anti-Ransomware
- Behaviour monitoring of files
- Protection against security vulnerabilities in installed software
- Online banking and browser protection
- Protection against malware and phishing when surfing
- Protection against manipulated USB devices
- DeepRay AI technology
- Light Agent for virtual machines
- Samba File Server Security
- Real-time protection
- Theft protection
- App and contact filter
- Software/hardware directory
- Simple (remote) administration with guideline inheritance
- Clear dashboard
- Deployment on non-dedicated server also possible
- Active Directory connection
- Multi-Tenancy
- Patch Management *optional purchase
G Data Antivirus Business

- Virus monitor with CloseGap hybrid technology
- Anti-Ransomware
- Behaviour monitoring of files
- Protection against security vulnerabilities in installed software
- Online banking and browser protection
- Protection against malware and phishing when surfing
- Protection against manipulated USB devices
- DeepRay AI technology
- Light Agent for virtual machines
- Firewall
- Patch Management *optional purchase
- Mobile Device Management
- Real-time protection
- Theft protection
- App and contact filter
- Availability & Performance
- Network Monitoring
- Data security & IT compliance
- Antispam
- Web content and Internet usage monitoring
- Device control
- Application control via blacklisting/whitelisting
- Client backup
- Server & Gateway Security
- Samba File Server Security
- Exchange Mail Security
- Linux Mail Security Gateway
- Linux Web Security Gateway
- Reporting & IT Audits
- Report Manager
- Software/hardware directory
- Simple (remote) administration with guideline inheritance
- Clear dashboard
- Deployment on non-dedicated server also possible
- Active Directory connection
- Multi Tenancy
